For many businesses, Microsoft 365 is a fantastic tool to use as it comes, known as “off the shelf”. A default tenant has a wide range of security features and settings pre-configured, allowing you to focus on your business instead of figuring out complicated security systems and studying a glossary of acronyms. From an ease-of-use perspective, these default settings let you get started using Microsoft 365 straight away with rich sharing and collaboration features.
But while the default configuration may work well to get started, does it truly keep you and your data secure long-term? Below we’ll break down some key settings that we recommend all Microsoft 365 customers change today to further secure themselves, by preventing data leaks and snooping from bad actors.
Unboxing a Microsoft 365 Tenant
Before we start talking about what to change, let’s take a look what you get when you buy a brand-new tenancy using Business Premium Licensing:
Single Factor Authentication
Out of the box MFA is enabled but not enforced! This means that a single leaked password could bring everything crashing down without any secondary identity checks.
No Conditional Access
On top of no MFA enforcement, there are no strict controls on login conditions for users. This means that any user could log in from anywhere in the world, and on any device. This leaves you wide open to attacks without any protections in place.
Generous Sharing Settings
Being able to share data externally with ease is great, but as your business grows this can quickly become a compliance concern. By default, sharing outside of your org will be completely allowed, with external parties typically being able to access shared company data with no verification checks perpetually. Even if you’re secure internally, can you trust recipients outside your business to never be compromised, granting access to your data?
Basic Email Filters
By default, you get some basic anti-spam and anti-malware filtering. However, additional features such as anti-phishing and URL rewrite features remain unconfigured which leaves you vulnerable to phishing incidents.
User Permissions
For ease-of-use Microsoft allow all users to register new 3rd party enterprise applications. These can be a great convenience when getting started, but down the line this can be abused by malicious actors who are seeking to put a permanent backdoor on your company’s data. Or, it could inadvertently result in data leakage to unapproved partners — in some instances this could be sensitive data fed into AI training models!
While many people assume that these platforms come completely secure at point of purchase, the reality is that convenience and usability can often take precedence over security. For organisations that are unable to secure and maintain their tenants, it can be easily to accumulate deep technical debt without making the required security changes.
How can I secure my Microsoft 365 tenant?
Hardening your tenant to a more secure state can be a daunting task for more non-technical users, however, there are some basic steps you can do today to start operating in a more secure manner.
We always recommend starting with multi-factor authentication (MFA). If your tenant was a cake, MFA would be the icing on top. It’s straightforward to set your users up with MFA — it can be done easily through self-service methods. Microsoft make this incredibly easy by visiting aka.ms/mfasetup (if you’re more hyperlink conscious, search for “Microsoft 365 setup MFA” in your search engine of choice). By default, you can use tools such as Microsoft Authenticator and SMS, or you can set up more modern methods like passkeys.
After this, start an audit of your Global Administrators. This is a role you can assign to an account that grants access to everything in your tenant and is assigned to the first account made in the tenant. For best practice it’s always recommended to have a separate account from your day-to-day account and should always be covered under multi-factor authentication. If using conditional access, consider building a more enhanced policy targeting all global admins that enforces logins from a certain location or a compliant device.
When it comes to email, it may feel like the same old technology it’s always been, but under the hood it’s gone through a lot of change over the decades. Microsoft are beginning to disable a lot of these in the background automatically, but it’s always worth a review to ensure you’ve disabled old authentication methods such as POP, IMAP, and SMTP AUTH – these older methods often do not support MFA at all, and some transmit data without encryption, meaning your data is vulnerable to man-in-the-middle (MITM) attacks.
Finally, as mentioned earlier, edit your user permissions in Entra to prevent your users from registering enterprise applications. This is a huge step towards “defence-in-depth” and helps stop hackers from embedding themselves deeper into your tenant, even if they could compromise a user account. It’s also quickly becoming a key data loss prevention policy, after all, keeping your data secure is more than just a compliance tick box!
These few steps represent only a microcosm of the changes that can be made to secure a tenant, but they represent a good immediate step you can make today to start securing your environment.
Set it and forget it?
Securing your tenant isn’t always as simple as ticking a box or filling in a page! We consider security an ever-evolving landscape where you need to be on top of the latest changes and features. Our first common pitfall to avoid is any idea of security being a “set and forget” exercise — it needs to be maintained and checked over time as threat actors evolve and change their strategies.
We recommended keeping the below in mind when dealing with your tenant’s security:
Don’t assume Microsoft are doing it all for you
Microsoft do a great job at configuring security defaults behind the scenes, and some of the recommendations you’ll see above are quickly become the new baseline in Microsoft 365. But ultimately, they are not responsible for your individual security, and the onus is on you to keep things secure.
Don’t switch features on without testing
Enabling new security features is also a great way to enhance your posture, but simply enabling features without a deeper understanding of impact can cause a lot of trouble. This could span from disrupting ongoing work, to data loss, or even a complete lock-out from your tenant in the case of a misconfigured conditional access policy. In worst case scenarios, it can take weeks to verify yourself and regain access.
Consider the user experience
This is one we see ignored most often. Security is a balancing act between itself and usability. Becoming a blockage to legitimate business flows can cause frustration and may cause individuals to look for workarounds outside of your security stack, resulting in shadow IT scenarios which we want to avoid.
Stay in the loop on security
In the UK, the National Cyber Security Centre (NCSC) will periodically publish new guidance on staying secure online. You can also subscribe to Microsoft announcements to see more tailored information to what may affect you coming down the pipeline.
What else can I monitor?
If you’re not also looking, turn your attention to your Microsoft Secure Score. Secure Score is a great built-in tool in 365 where Microsoft issue guidance and steps to secure your environment further. This is built in and free for all Microsoft 365 customers and can be accessed from the Defender portal under “Exposure Management”. You’ll see a list of actionable items with steps to improve them. Microsoft tag each improvement with an improvement score, so you can easily see and action what’s the most important to address. It’ll look something like below:
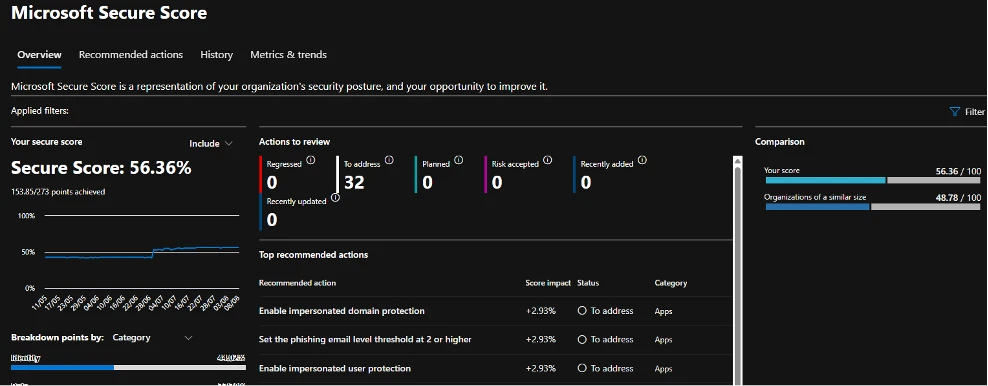
Secure Score is incredibly user friendly and can make tenant security much more palatable for non-IT teams. It can also highlight if you have the correct licensing required to meet security requirements, so you can assess if you need to upgrade your licensing to enhance security.
Ultimately, off-the-shelf Microsoft 365 remains an incredibly powerful platform — but not a fully secure one. With just a small amount of work, a wide range of security enhancements can be applied to your tenancy which will give you the edge when bad actors come looking. Look at features such as MFA, conditional access and sharing permissions to solve some of the most common attack vectors bad actors use to infiltrate Microsoft 365 environments.


